
The pandemic brought on a wave of companies to go remote. The switch happened so quickly; that many employers were not ready for this transition. Companies saw a spike in cyber-attacks and a breach of security during 2020.
“IAM challenges have become increasingly complex, and many organizations lack the skills and resources to manage effectively. Leaders must improve their approaches to identity proofing, develop stronger vendor management skills and mitigate the risks of an increasingly remote workforce.â€
Akif Khan, Senior Director Analyst, Gartner
Top trending IAM practices in 2022
2022 is here, and that means it’s time to start thinking about the top identity and access management (IAM) practices for the year. IAM is more important than ever before, as businesses are increasingly moving to the cloud and sharing data between different platforms. In this article, we discuss some of the most important IAM trends for 2022 and how to prepare your business for them. Stay ahead of the curve and make sure your IAM program is ready for whatever comes next!
What is IAM?
IAM is a process of managing user identities and their access to resources. Such as security badges and key cards, or through digital means, such as passwords and two-factor authentication. IAM is important for businesses of all sizes, as it helps to protect data and prevent unauthorized access to resources.
Components of IAM
There are three main components of IAM:
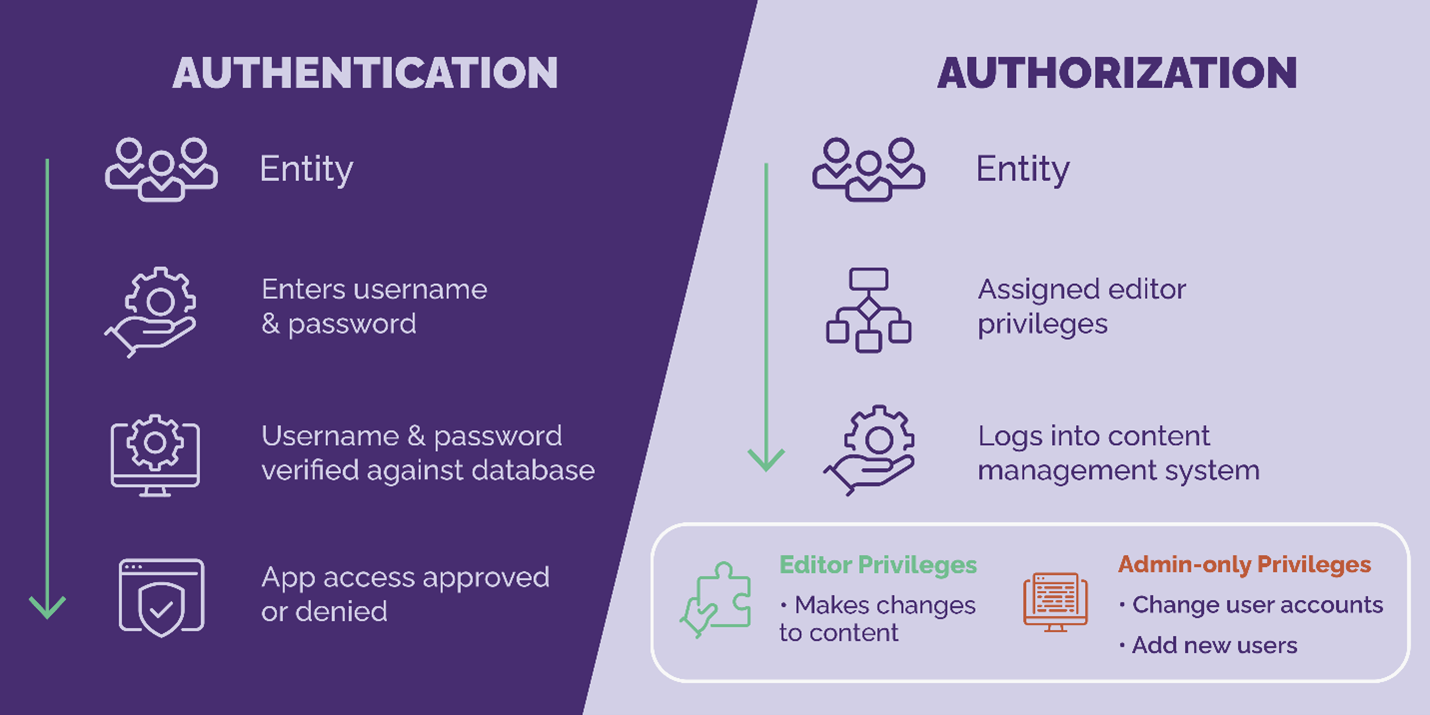
- Authentication: This is the process of verifying that a user is who they claim to be. This can be done through something as simple as a password or PIN, or more advanced methods such as biometrics or two-factor authentication.
- Authorization: This is the process of determining what a user is allowed to do once they have been authenticated. This is done through role-based access control, which defines what users can do based on their position within the company.
- Audit: This is the process of tracking and logging all IAM activity. This helps to ensure that policies are being followed, Above all any unauthorized access is detected and dealt with.
Challenges in implementing IAM in a working business
There are several common challenges that businesses face when implementing IAM:
- Lack of budget: IAM can be a costly endeavor, especially if you are starting from scratch. It is important to allocate enough resources to your IAM program to ensure its success.
- Lack of governance: IAM can be complex and difficult to manage. Therefore without proper governance, IAM can quickly become a burden for your IT staff.
- Lack of awareness: IAM is often seen as a technical issue when in reality it is a business issue. IAM should be treated as such, and all employees should be made aware of its importance.
The future of IAM
Some of the top IAM trends for 2022 include:
- Cloud identity management: As more businesses move to the cloud, IAM needs to follow suit. This means managing user identities and access from a central location, as well as integrating with other cloud-based applications.
- Artificial intelligence: AI can automate Password resetting and account provisioning. This helps to improve IAM efficiency and reduce the burden on IT staff.
- Blockchain: Blockchain technology can secure IAM data, For instance, passwords and biometric information. This is an important trend to watch as businesses become more reliant on IAM.
Another IAM trend for 2022 is the rise of identity as a service (IDaaS). IDaaS is a cloud-based IAM solution that provides all the same benefits as traditional IAM programs, but with added flexibility and scalability. This is an important trend to watch for businesses of all sizes, as it helps to improve IAM efficiency and reduce IAM costs.
The use of IAM in the public sector
Identity and access management (IAM) is not just important in the private sector, but especially useful in government. IAM does not just add high security, it also ensures the consistency and trustworthiness of services, as technology advances.
Recently, the Office of Management and Budget (OMB) updated the federal government’s identity, credentials, and access management (ICAM) policy. It is no longer effective to just create a checklist of security mandates to oppose cyber-attacks. This update requires agencies to use IAM as the foundation for preventing attacks. IAM prevents hackers’ attempts to access federal resources. After a huge security breach back in 2015, the federal government launched a 30-day cybersecurity sprint to assess and improve the health of federal information technology (IT) occurred. Since then, the government has continued to increase its IAM security metrics, But with hackers getting smarter, increasing IAM measure becomes more pertinent.
Government agencies must learn the security threats they face and drive digital identity techniques that secure local, state, and federal agencies’ data.
Are you ready for this year?
By staying up-to-date on the latest IAM trends and technologies, you ensure that your IAM program is ready for whatever comes next. Contact us today to learn more about how we can help you prepare for the future of IAM!
About Centurion Consulting Group
Centurion Consulting Group, LLC, a Woman-Owned Small Business headquartered in Herndon, VA conveniently located near Washington D.C., is a national IT Services consulting firm servicing the public and private sector by delivering relevant solutions for our client’s complex business and technology challenges. Our executive team has over 25 years of experience individually, including over 10 years of direct business partnership in the IT staffing, federal contracting, and professional services industries.
Centurion’s leaders have demonstrated expertise throughout the past three decades in partnering with over 10,000 consultants and hundreds of clients – from Fortune 100 to Inc. 5000 firms – in multiple industries including banking, education, federal, financial, healthcare, hospitality, insurance, non-profit, state and local, technology, and telecommunications. www.centurioncg.com
